IT infrastructure serves as the foundation for all business activities and accumulates various types of information. The leakage of this information to external parties has the potential to cause significant damage to companies and organizations. For instance, if personal information or company confidential information are leaked, they can be exploited, or end up in competitors' hands, causing severe damage to the company or organization.
In this article, we will explore the vital reasons to prioritize cyber security when setting up IT infrastructure. We will also share the actual case studies of company who faced the damages and6 security measures that can secure your organization.
There are 4 major reasons why cyber security measures are important in IT infrastructure development.
1. Minimizing Security Risks
IT infrastructure contains critical information such as confidential data and personal information. If you develop IT infrastructure without implementing cyber security measures, the risks of information leakage and hacking increase. By appropriately implementing security measures, these risks can be reduced.
2. Compliance with Legal Regulations
In many countries, laws regarding information security, such as personal information protection laws and cyber security laws, have been enacted. Compliance based on these laws is also required in IT infrastructure development. By implementing appropriate cyber security measures, you can comply with legal regulations and avoid penalties due to improper information leakage or cyber-attacks.
3. Polishing Your Corporate Image
Companies that have sufficient cyber security measures in place are perceived as having a lower risk of security-related issues or incidents, which contributes to an improved corporate image. Conversely, companies with inadequate security measures face risks such as impacts on transactions due to not meeting the level demanded by customers, and potential conflicts with business partners in the event of an incident.
4. Keeping the Business Wheels Turning
It is also important for cyber security measures to ensure that the system continues to operate normally even if the IT infrastructure is attacked. If a system goes down due to a cyber-attack, it can affect the continuity of the business. For example, for companies that provide online services, a temporary halt in services could result in a loss of customer trust, necessitating a swift response to recovery. By preventing information leakage, data tampering, and unauthorized access to the system by malicious attackers, you can ensure the safety of the system.
Business leaders and IT departments are called upon to implement effective security measures, taking into account the perspectives discussed.
Beyond the direct damages inflicted by cyberattacks, there's a cascading effect: investigating the root causes, repairing the damages, and communicating with business partners, customers, and stakeholders. The costs associated with these post-incident actions can be staggering, to the point where the viability of the business is in jeopardy. The extent of damage from cyberattacks often surpasses expectations and can result in substantial losses. Ultimately, this leads to financial losses, eroding customer base, and hindrances in business continuity, which collectively elevate the overall business risks for the company.
|
|
|
business continuity |
◆ Case 1 : Damage case at a plastic parts manufacturing company
Hackers took control of the company's email server and sent out deceptive emails to clients, posing as the company.
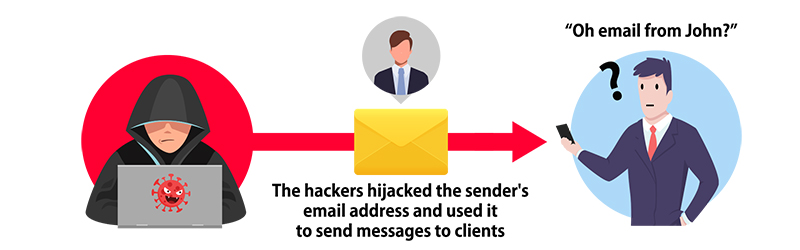
<Details of the Damage>
This was a case where the email server's vulnerabilities led to the use of genuine email addresses in deceptive 'spoofed' emails. The company received a notice from a client saying, “We received an email from you, but it was flagged as phishing.” Upon checking the email sending history, it turned out that the employee who supposedly sent the email didn’t actually send anything. Instead, hackers had taken control of the email server and were sending out deceptive 'spoofed' emails to clients while pretending to be the company.
Had this not been discovered in time, there could have been a ripple effect. The fraudulent activity could have impacted more clients, causing the company’s reputation to take a nosedive as trust would have been severely undermined.
<Cause>
The primary cause was due to the vulnerabilities in the email server
<Action Taken>
・Make sure to always keep the software up-to-date with the latest versions.
・Before using any software in-house, have it double-checked by the tech team to ensure it’s safe.
・Thoroughly raise awareness within the company about the importance of IT system management.
◆ Case 2 : Damage case at an automobile parts manufacturing company
The manufacturing line was temporarily shut down due to a targeted attack through spam emails
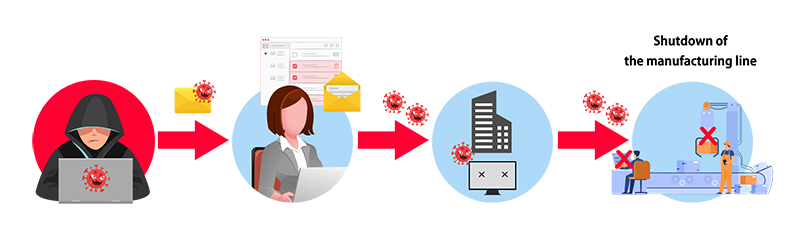
<Details of the Damage>
A staff member in charge of procurement received an email that appeared to be from a shipping company, asking to verify the shipment status of materials. The staff member clicked on a link in the email, which led to the computer being infected with ransomware. As a result, all files on the computer were locked, making it impossible to access or retrieve data. The infection also spread to the company's internal data, affecting various systems involved in production. As a result, the manufacturing line had to be temporarily shut down. The company reported substantial financial losses and a negative impact on annual sales.
<Cause>
Weak security measures
<Action Taken>
・Educate employees about cybersecurity awareness, including how to recognize and handle spam and phishing emails.
・Review and strengthen the security settings of backend systems.
6 Security Measures
As IT technology continues to advance, so does the evolution of cyber attack techniques. To minimize the impact of such attacks, it is crucial to prioritize the thorough implementation of the following six major countermeasures, considering the possibility of being targeted by cyber attacks.
|
Security Measures |
Security Measures |
Security Measures |
|
Security Measures |
Security Measures |
Policy (Security Policy) |
In the next article, we will provide specific explanations of six examples of security measures
We offer services to investigate and diagnose the security vulnerabilities in your infrastructure, and we can provide you with appropriate security measures tailored to your specific needs. If you have any questions or inquiries, please feel free to contact us.
09-06-2023