Measure 1 : Physical Security Measures
Measures to protect against physical interference (such as information theft or loss) with facilities, equipment, and assets
[ Examples of Measures ]
- Management of entry and exit to the premises, biometric authentication, installation of surveillance cameras.
- Servers and network equipment are stored in a secured server room with locked doors.
- Encryption of hard drives and USB memory devices used for computers taken outside the premises.
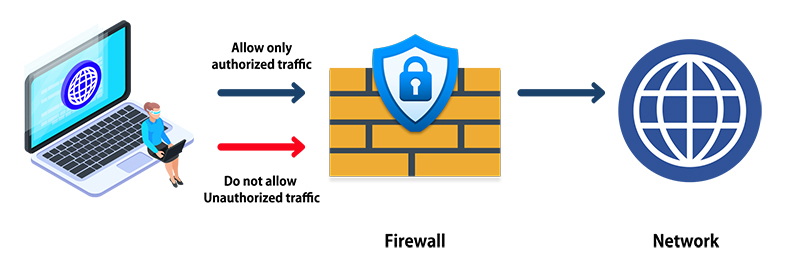
Measure 2 : Network Security Measures
Implementing a firewall management system to block access to internal systems from external networks and manage user access. Firewalls serve the purpose of preventing unauthorized access to internal systems and controlling user access.
[ Examples of Measures ]
- Install a firewall at the boundary point between the external network and the internal network.
- There is a system in place to promptly apply configuration changes or software patches to address new threats.
- The functionalities of the firewall are enabled and active.
✓ Web filtering (blocking access to malicious websites) is implemented.
✓ Intrusion Detection System (IDS) is in place.
✓ Intrusion Prevention System (IPS) is deployed.
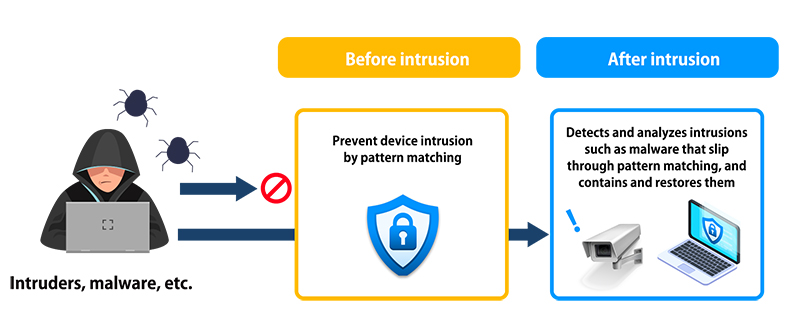
Measure 3 : Endpoint Security Measures
Security measures to prevent information leakage from devices at the endpoint of IT systems, such as malware intrusion, unauthorized access, and cyber attacks.
◆ Examples of endpoint devices
- Desktop computers
- Laptop computers
- Devices such as smartphones and tablets
- Wearable devices such as smartwatches and smart medical devices
- Network peripherals such as printers, scanners, and copiers
- Workstations and servers
- Routers and switches
- Internet of Things (IoT) devices such as smart sensors and other smart machines
[ Examples of Measures ]
- Measures for protection
✓ Installation of pattern-based malware detection software
✓ Deployment of behavior-based malware detection software
✓ EDR (Endpoint Detection and Response) for monitoring suspicious activities and logging
✓ DLP (Data Loss Prevention) for data monitoring and leakage prevention
✓ USB device control and management
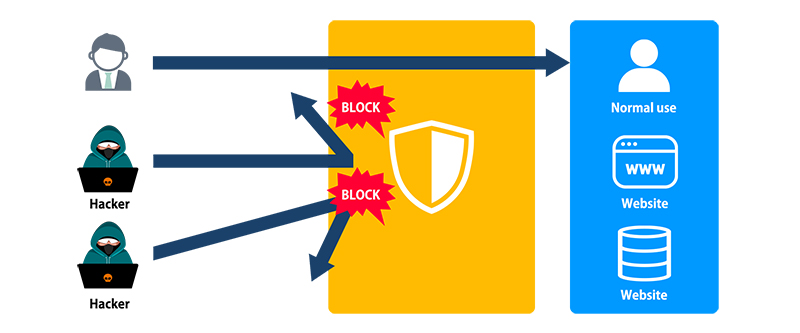
Measure 4 : Application Security Measures
Application-level security measures to protect against data theft, code injection, and hijacking within applications
[ Examples of Measures ]
- Obtaining the latest vulnerability information related to the used applications
- Prompt implementation of countermeasures against vulnerabilities and applying the latest security updates
✓ Checking the update application process before applying the updates
✓ Preparing application testing procedures after applying the updates
Measure 5 : Data Security Measures
Measures to ensure the secure protection of corporate data stored in various locations such as computers and servers, safeguarding against unauthorized access, data corruption, theft, and other threats.
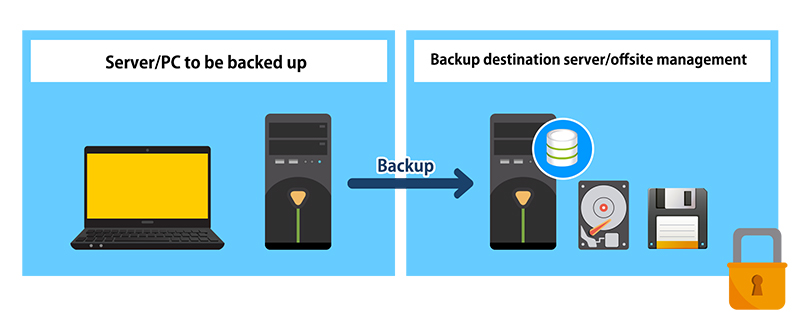
[ Examples of Measures ]
- Data protection through backup
✓ Regular data backups on a daily, weekly, and monthly basis
✓ Encryption of backup data for enhanced security
✓ Off-site management of backup data to ensure redundancy and disaster recovery
✓ Conducting rehearsals for data and system restoration to ensure smooth recovery processes
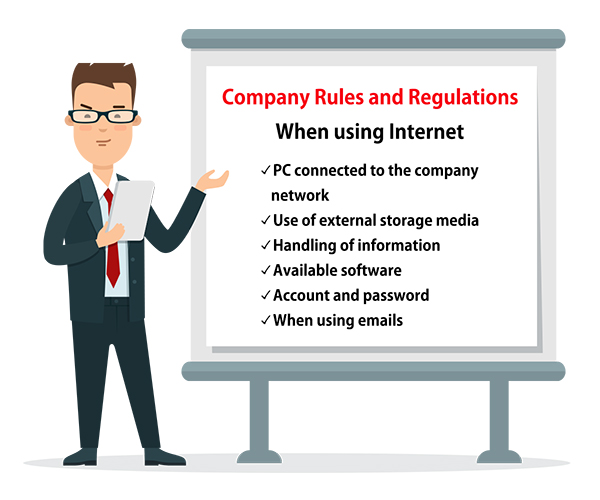
Measure 6 : Organizational Security Policy (Security Policy)
Even with the implementation of the aforementioned security measures, efficient security management is not possible without proper organizational management policies. It is crucial for organizations to document and articulate their information security policies to ensure clarity and adherence
[ Examples of Measures ]
- Creation of various security regulations for employees
✓ Guidelines for using computers connected to the internal network
✓ Policies regarding the use of external storage media
✓ Procedures for handling sensitive information
✓ Approved software usage policies
✓ Guidelines for managing accounts and passwords
✓ Email usage
Please feel free to contact us for more information.